by Mark Maunder of Wordfence
Google’s Chrome web browser is used by over 50% of users on the web. When you visit a website that is using SSL, otherwise known as HTTPS or TLS, you see a green message in your browser location bar that says “Secure”.
“Secure” in Chrome browser does not mean “Safe”. In this post I will explain why in terms that are easy to understand and tell you what to do about it. I’ve written this post to be easy to read. I’d like to encourage you to share it with friends and family to help them stay secure.
For our technical readers, here is a summary of what we discuss in this post:
- We show that SSL certificates are being issued by more than one certificate authority (CA) to phishing sites pretending to be Google, Microsoft, Apple and other well-known companies.
- A valid certificate causes Chrome to show a website as “Secure”.
- When a certificate is revoked once a CA realizes they should not have issued it, we show that Chrome still shows the site as “Secure”. The “revoked” status is only visible in Chrome developer tools.
- Malicious sites that have been issued valid SSL certificates take some time to appear on Chrome’s malicious site list. We show that the safe browsing list can not be relied on as a backup mechanism to protect users from malicious sites with valid SSL certificates.
What does “Secure” actually mean in Chrome browser?
In order for a website to be labeled as ‘Secure’ by Chrome, it needs to set up SSL on its web server. As part of that process, it needs to contact a certificate authority (CA) to get a ‘certificate’. The CA is supposed to verify that the website owner actually owns the website. This process is called ‘domain validation’. Other than verifying that the domain owner actually owns the website, the CA is not required to do anything else.
In Chrome, when you see “Secure” in your browser location bar, it means that the connection between your browser and the website you are connected to is encrypted. It also means that the person who installed the certificate on the website actually owns the site domain. It does not mean that the domain is “Trusted”, “Safe”, “Not malicious” or anything else.
LetsEncrypt is providing valid SSL certificates to phishing sites
Until relatively recently, CAs would generally not issue an SSL certificate to a site that is obviously trying to pretend it is apple.com or microsoft.com. However, there is a new CA called LetsEncrypt which issues free certificates to websites who want to use SSL.
LetsEncrypt has a noble goal. They are trying to make it free to use SSL to encrypt connections on the Web. However, they do not check to see if the website owner is pretending to be someone else. So the effect of this is that we are seeing many phishing sites that have a valid certificate issued by LetsEncrypt and which appear as ‘Secure’ in the Chrome browser.
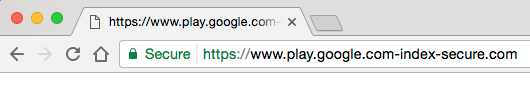
Here’s an example of a website that is using a LetsEncrypt certificate and which appears as ‘Secure’ in Chrome. At the time of writing this (1am PDT on March 28th, 2017) this site was not listed as malicious by Chrome or the Google Safe Browsing list and is shown as ‘Secure’.
As you can see, Chrome says the site is ‘Secure’. The site owner is trying to pretend the site is the Google Play store. They are hoping that you will confuse the text after ‘.com’ with what usually appears after the forward slash on the actual Google Play store. This is an example of a phishing site that will try to trick you into entering your Google Play Store login credentials.
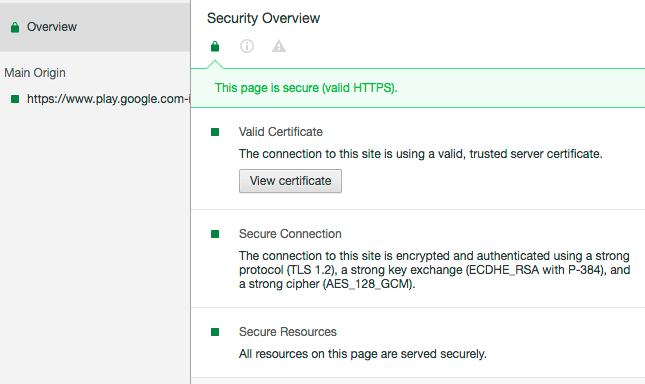
To view the information about this site’s certificate, you need to open up Chrome’s developer tools and view the security tab. You can do this by going to the View > Developer > Developer Tools menu.
Here’s what the developer tab looks like:
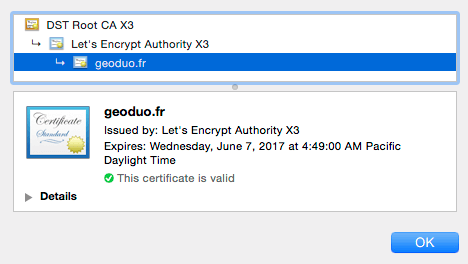
If you click “View certificate” here is what you see:
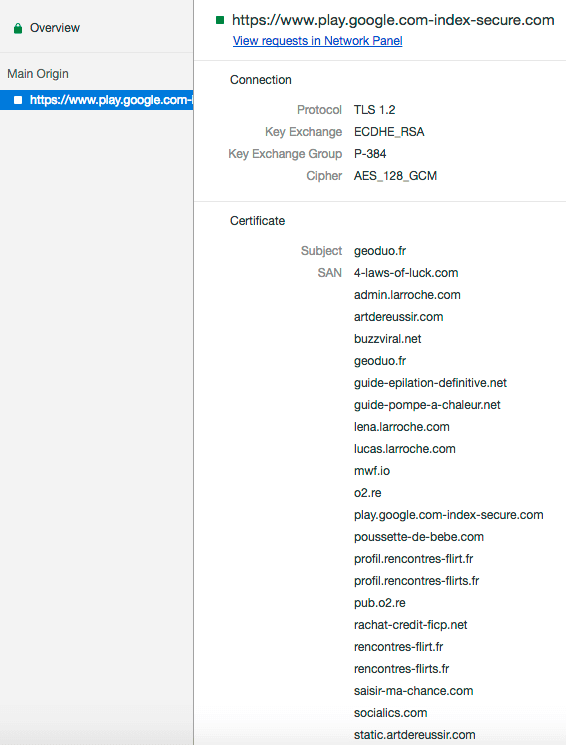
The certificate is listed as belonging to geoduo.fr but it is in fact used by many other websites. In the network tab you can see that list of sites: (Showing just the first few)
All of these sites share the same certificate. This can mean several things. It may mean that they are operated by the same individual. It can also mean that the hosting provider who hosts this site, OVH SAS France in this case, issued a free certificate to this site and lumped a lot of other sites into the same SSL certificate.
As you can see, “Secure” in this case simply means that you are talking to a malicious website using an encrypted connection. It does not mean the site is “Safe”.
The Problem is not just LetsEncrypt. It is other certificate authorities (CAs) too.
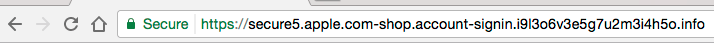
This problem is not just confined to LetsEncrypt, although they are by far the most common CA that phishing sites are using now. In the example below, the website is pretending to be Apple.com so that it can steal your Apple login credentials:
At the time of writing (March 28th at 1am Pacific Time) this site was not listed in the Google Safe Browsing list and Chrome was showing it as “Secure”. In this case the certificate was issued by Comodo.
Even if a CA revokes a certificate, Chrome still shows it as “Valid” and “Secure”.
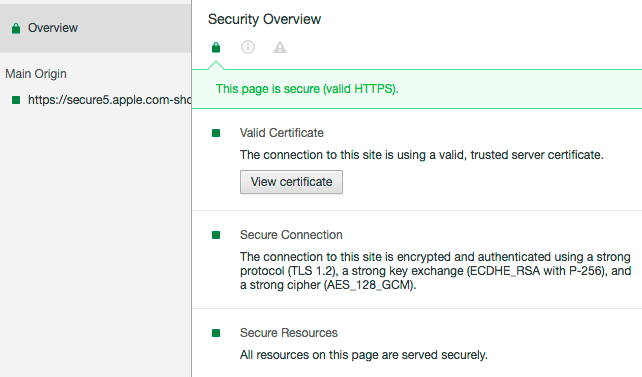
Let’s take a look at the Comodo certificate in the above example. First we go to ‘Dev Tools’ in Chrome and open the ‘Security’ tab:
As you can see the Security Overview says the page is “secure”. Now let’s click on “View certificate”:
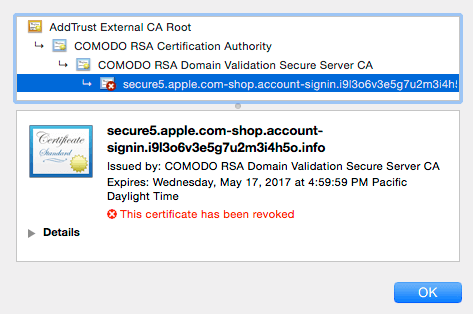
It turns out that this certificate has been “revoked”. What that means is that Comodo, the CA in this case, realized that the certificate belongs to a malicious website after they issued it and they decided to mark it as invalid.
Because Chrome does not check certificate revocation lists in real-time, it shows the certificate as valid in the location bar and the site as “Secure”. Chrome is unaware that Comodo has revoked the certificate after Comodo realized they should not have issued it in the first place.
You can’t rely on Chrome’s malicious site warnings from the Google Safe Browsing List
To do the research for this post, we used a service called Censys.io to look up certificates for websites that match specific patterns. Then we found other domains that are using the same certificates. Domains that share certificates are often related and may have the same owner.
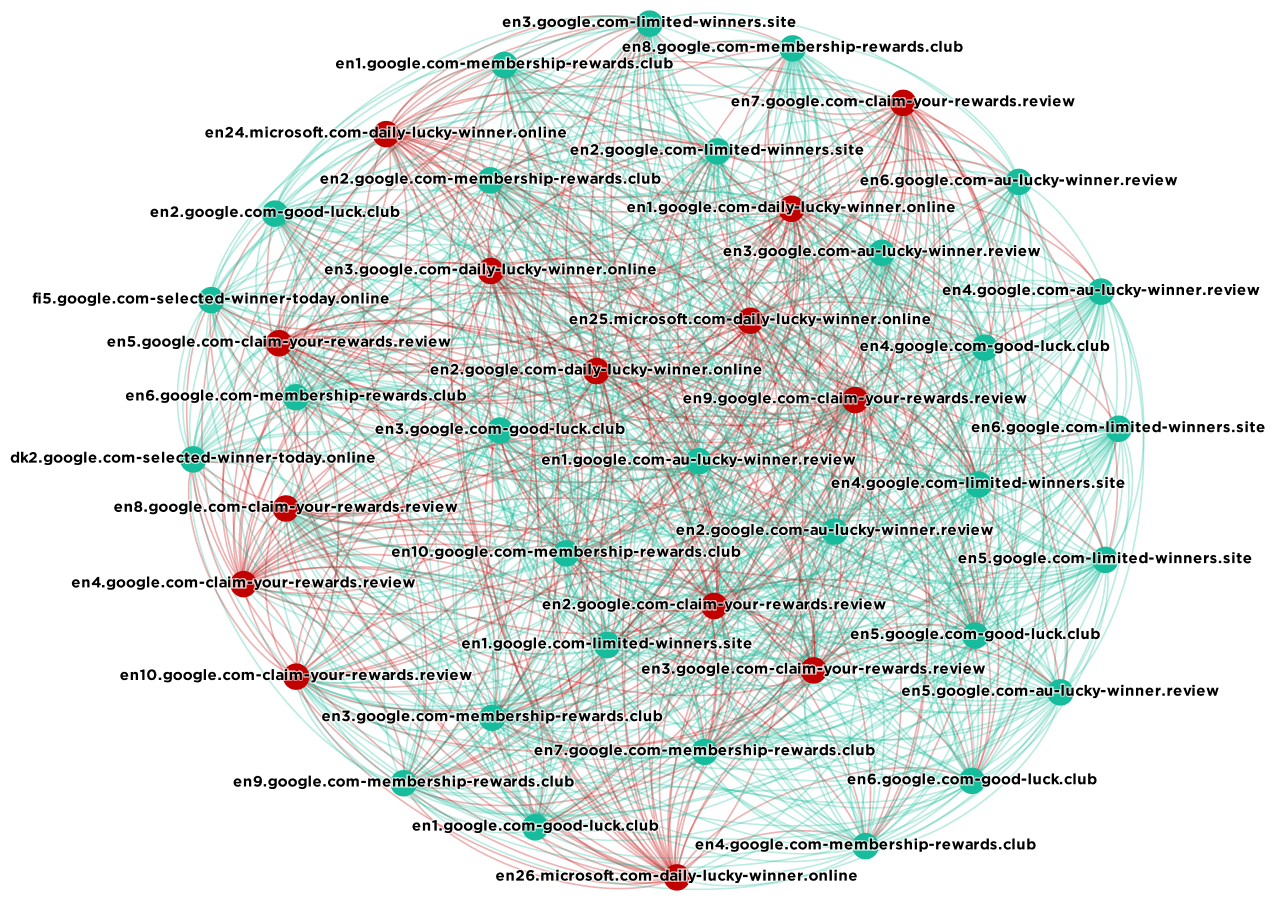
The following is a graphic that shows a number of phishing domains we found in our research that are sharing certificates. In the graphic below, domains that are marked as malicious by Chrome are in red. The rest are green. The lines link domains that share SSL certificates.
As you can see the domains in this list are pretending to be either google.com or microsoft.com. Click the graphic for a larger view. Some of them are listed as malicious by Google’s Chrome browser. Most of them are not listed as malicious.
The good news is that these domains will eventually end up on Google’s “safe browsing list” which is what Chrome uses to identify bad sites. This list was generated on the morning of Monday March 27th and by the evening some of the green domains above were appearing on the Google Safe Browsing list and Chrome was warning about them. But it does take time.
While the Safe Browsing project that Google runs does great work, Chrome users can not rely on it to reliably identify malicious sites and throw up a warning.
What should you do to ensure you stay safe on the web?
The best way to protect yourself against malicious sites, in this case, is to check your web browser’s location bar and read the full website hostname that appears there.
Look at the location bar above. You should see ‘https://www.wordfence.com/….’. When visiting any website that you plan to exchange sensitive data with, check the full hostname after ‘https://’ and before the next forward slash. If you don’t recognize it or if it looks like it has some weird stuff on the end, close the window immediately and think carefully about how you ended up on that website.
Avoid clicking whatever link brought you to that website again.
What can Google Chrome do to improve security?
In my opinion Google actually does a pretty good job of staying on top of things. They responded quickly to our post earlier this year about a new Gmail phishing scam. They reached out to contact us and fixed the issue.
Chrome must start looking up certificate revocation lists in real-time to fix the Comodo certificate issue we showed above. Having Chrome show a revoked certificate as “Secure” is not acceptable. However, doing this has performance penalties for Chrome users and it may also have privacy implications as websites that are visited are sent to CAs during the lookup. So it’s not a simple fix.
I’d like to see the Google Safe Browsing (GSB) team using certificate relationships as we have used above to identify other malicious domains that should be on the GSB. They may be able to automate this. This will speed up the time it takes to get malicious sites listed on the GSB.
I don’t think the “Secure” designator in the Chrome location bar is good enough. The Chrome team should consider a sliding scale that takes into account who the CA is, how many domains share the same certificate and the age of a domain and its certificate. There are other signals they can probably incorporate to produce a security score, rather than just a binary “Secure” or “Not Secure” designator for websites.
What can LetsEncrypt do to improve security?
The LetsEncrypt team must start doing keyword searches on SSL certificate applications. This can be fully automated and LetsEncrypt needs to reject certificates that contain strings like “.apple.com.”, “.paypal.com.”, “.google.com.” and other common phishing patterns.
They could implement a review process where, if your certificate request is rejected, you can apply for a token which lets you bypass the check in future once you prove you need something with “.apple.com.” in it.
What about other CAs like Comodo?
In the example we provided above, Comodo actually realized the site was malicious and revoked the certificate. So they should be given credit for doing that. The problem was that Chrome does correctly look up revoked certificates.
The way CAs issue certificates has been a source of debate for some time. Google has put a proposal on the table to revoke Symantec’s ability to issue certificates based on a history of bad CA behavior from them. The proposal suggests immediately revoking Symantec’s ability to issue EV (extended validation) certificates and to gradually mistrust regular SSL certificates issued by them.
There is a constant and lively debate between browser makers and CAs about how certificates should be issued and what constitutes a valid certificate.
Spread the word!
As browsers try to improve the way they represent the security of sites and CAs try to improve their processes, you can help secure the web by making sure you actually look at the hostname that appears in the location bar. Here is what a hostname looks like. It is the underlined part of the URL:
Make sure:
- You can see the entire hostname in the browser location bar.
- You recognize the entire hostname.
- Your browser says that your connection is encrypted. Chrome will show the word “Secure”.
Share this message with those you care about. Less technical users may see the word “Secure” and think it means the site is “Safe”. It does not. By explaining to your friends and family what a ‘hostname’ is in the location bar and getting them to double check it, you will probably save at least one person from being the victim of a phishing attack.
Credits: Thanks to Wordfence team member Sean Murphy who did the original research connecting malicious sites through their shared certificate use and developed the graph visualization. He also generated the data for this post. Thanks to Dan Moen for editing.